The Level of Security These Days
-
March 25, 2022 at 12:00 am
Comments posted to this topic are about the item The Level of Security These Days
-
March 25, 2022 at 12:25 pm
Brute force works if the protected system allows an unlimited number of retries, no time restrictions on subsequent attempts (see iPhone), and no alerts to the genuine user of attempts.
As computing power increases, will we eventually need 64-character passwords? Do we expect the layman to be able to manage/remember these? I’m an old guy and I struggle with 8 or 10.
-
March 25, 2022 at 12:36 pm
I was reading an article about MFA security a few months ago. It was quite interesting because you'd think that is a good idea. However, there are now hackers that can get your phone number moved to another phone and then they have MFA to your accounts and you are dead in the water. The article stated that phones were never intended to be a form of verification for security and how phone companies are not equipped all of the time to catch bad actors switching phone numbers to other phones/carriers.
-
March 25, 2022 at 2:31 pm
I think it's a TV trope that a clever hacker can somehow guess your password or brute force it with a script. What's really going on is that folks re-use the same password across multiple applications, and then a single data breach results in their login credentials ending up on a list for sale on the dark web. Another vector of attack is un-secure wifi connections or spyware that hackers can use to steal credentials.
"Do not seek to follow in the footsteps of the wise. Instead, seek what they sought." - Matsuo Basho
-
March 25, 2022 at 3:31 pm
phegedusich wrote:Brute force works if the protected system allows an unlimited number of retries, no time restrictions on subsequent attempts (see iPhone), and no alerts to the genuine user of attempts.
As computing power increases, will we eventually need 64-character passwords? Do we expect the layman to be able to manage/remember these? I’m an old guy and I struggle with 8 or 10.
Most systems don't allow unlimited tries, though I don't know I'd want to test that on many random websites. More, the concerns are a loss of passwords that are reused. I.e. you use a password for SSC here and we lose the db, but you've used that pwd, or a variation for your email, bank, etc. That's the brute force concern.
For length, yes, we will need longer ones. I don't know 64char is coming anytime in my lifetime (50s), but I could see 20 needed. While there are good techniques (sentences, etc.), really, a password manager is what is needed for most of us. Yes, you could lose the safe, but again, brute force. Remember one 24 character password and you're likely fine.
-
March 25, 2022 at 3:33 pm
Somebody wrote:I was reading an article about MFA security a few months ago. It was quite interesting because you'd think that is a good idea. However, there are now hackers that can get your phone number moved to another phone and then they have MFA to your accounts and you are dead in the water. The article stated that phones were never intended to be a form of verification for security and how phone companies are not equipped all of the time to catch bad actors switching phone numbers to other phones/carriers.
More modern MFA systems are not using SMS. While some are, some are using apps and other factors. My MS one either requires an approval from an app, or me to select a number and confirm a login on the device.
Even if someone can move your number, it's unlikely, and it's not a reason to avoid using those. Security is a series of layers, and this adds one more.
-
March 25, 2022 at 3:34 pm
Eric M Russell wrote:I think it's a TV trope that a clever hacker can somehow guess your password or brute force it with a script. What's really going on is that folks re-use the same password across multiple applications, and then a single data breach results in their login credentials ending up on a list for sale on the dark web. Another vector of attack is un-secure wifi connections or spyware that hackers can use to steal credentials.
^^^^^ THIS!!!!! I had to get on my wife about this, and lightly chastise my Mom. Stop reusing passwords. It's not the bank that likely loses it, it's someone else.
-
March 25, 2022 at 4:55 pm
I don't mind the MFA so much except when it involves more than one device. I am NOT addicted to a cell phone, and when they send some stupid code to the phone and it is in the other end of the house, I get sort of 'irritated'. (Read that 'pissed')
I usually don't mind all the irrelevant questions so much. And while I do reuse passwords, I make them longer, such as combining house numbers/zip codes from places I've lived decades ago along with special characters, etc. as these are pretty easy to remember and the hints can help, such as street names, towns, etc. These are OK as long as they aren't in my credit report history.
To me the larger issue is credit card fraud to which I've been subjected at least three times, but my CC company is very good at getting things settled and I've had no bad experiences with them. And I use their ability to get a text/email notice when the card is used.
MFA is a good thing IF it is well designed
Rick
If you do a half-assed job of things, folks will ask 'why did this ass only do half the job?' -
March 25, 2022 at 7:42 pm
A lot of these are well designed, but if you're saying they are inconvenient, I think that's part of the challenge. The phone not being near you is a pain, but it also provides security.
I think Apple has done an intersting thing as a notification appears on different devices, so a strange sign on would ping an iPhone, or an iPad, or an iMac. Inside an ecosystem for sure, but I like that. I also find that I can keep Google Messages connected on my PC, so if my phone is elsewhere (car, bedroom, etc), I can get codes. I also like the auth apps, which can be deployed in a few places.
There is a need, however, to have another verification method, so you'd need some sort of device.
-
March 25, 2022 at 7:53 pm
Steve Jones - SSC Editor wrote:phegedusich wrote:Brute force works if the protected system allows an unlimited number of retries, no time restrictions on subsequent attempts (see iPhone), and no alerts to the genuine user of attempts.
As computing power increases, will we eventually need 64-character passwords? Do we expect the layman to be able to manage/remember these? I’m an old guy and I struggle with 8 or 10.
Most systems don't allow unlimited tries, though I don't know I'd want to test that on many random websites. More, the concerns are a loss of passwords that are reused. I.e. you use a password for SSC here and we lose the db, but you've used that pwd, or a variation for your email, bank, etc. That's the brute force concern.
For length, yes, we will need longer ones. I don't know 64char is coming anytime in my lifetime (50s), but I could see 20 needed. While there are good techniques (sentences, etc.), really, a password manager is what is needed for most of us. Yes, you could lose the safe, but again, brute force. Remember one 24 character password and you're likely fine.
The thing is bad password practices(reusing passwords across places that have questionable security) or insecure infrastructure(key loggers, social engineering etc..) doesn't care about how complex your password is. And on systems that do have limited retries a relatively short password with very basic requirements(upper and lowercase and a number say) is more than adequate to stop brute force.
-
March 27, 2022 at 6:52 pm
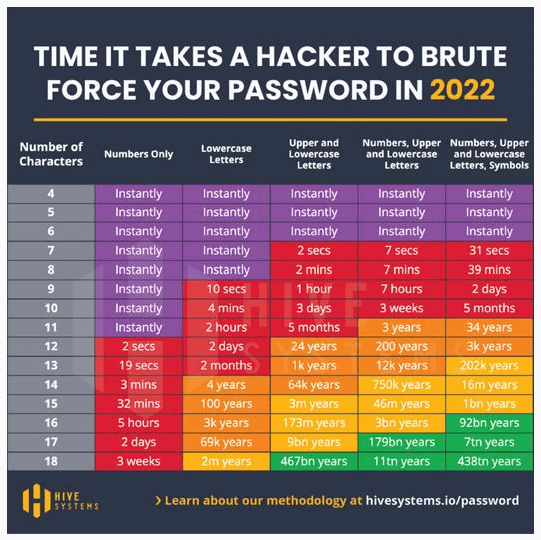
I found the following chart a few days ago. It's based on "unlimited" attempts instead of a "3 strikes and you're out" methodology.
I'm also not sure of what hardware they estimate this for. We invited some folks to come in to demonstrate that 8 byte passwords were and easy hack. They use a 64 GPU machine running at very overclocked speeds (heh... and burned one up in the process). I don't remember the exact amount of time it took but I can tell you for sure it was a heck of a lot less than 39 minutes advertised in the right column of the poster above. They also did 12 byte passwords in less than 30 minutes.
Of course, they didn't have to contend with "3 strikes and you're out" for the test, either.
--Jeff Moden
RBAR is pronounced "ree-bar" and is a "Modenism" for Row-By-Agonizing-Row.
First step towards the paradigm shift of writing Set Based code:
________Stop thinking about what you want to do to a ROW... think, instead, of what you want to do to a COLUMN.Change is inevitable... Change for the better is not.
Helpful Links:
How to post code problems
How to Post Performance Problems
Create a Tally Function (fnTally) -
March 27, 2022 at 7:37 pm
Jeff, I saw that same chart, and thought it was very interesting and informative. Thanks for sharing it with everyone here. I need to share it with my three sons who are all in IT careers too.
Rick
If you do a half-assed job of things, folks will ask 'why did this ass only do half the job?' -
March 28, 2022 at 4:40 pm
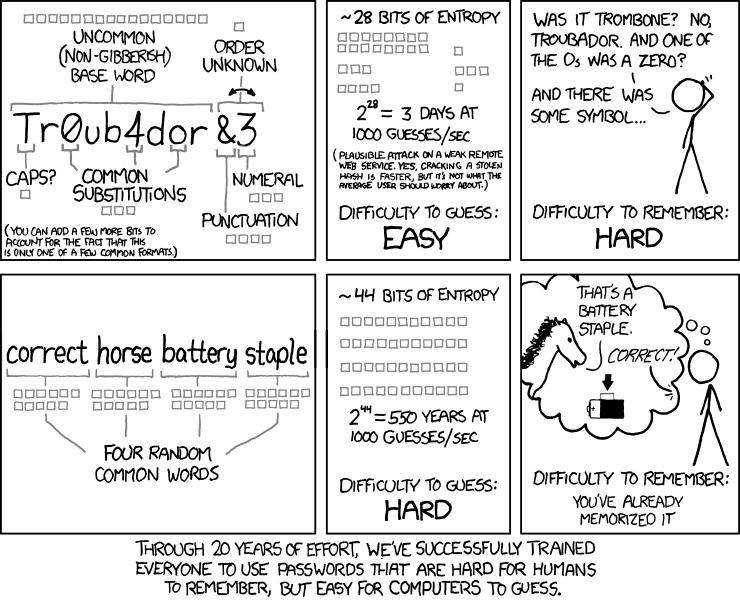
I like that chart Jeff, I might add it to my favourite argument I trot out every time I am faced with a short password requirement that forces numbers, capitals etc.
I am sure everyone is aware of it, the "Correct Horse Battery Staple" XKCD cartoon, but if not...

Should point out, I usually add a Latin word to help mitigate dictionary attacks and where I am constrained capitalise etc.
- This reply was modified 3 years, 11 months ago by david.edwards 76768.
- This reply was modified 3 years, 11 months ago by david.edwards 76768.
"Knowledge is of two kinds. We know a subject ourselves, or we know where we can find information upon it. When we enquire into any subject, the first thing we have to do is to know what books have treated of it. This leads us to look at catalogues, and at the backs of books in libraries."
— Samuel Johnson
I wonder, would the great Samuel Johnson have replaced that with "GIYF" now? -
March 29, 2022 at 2:13 pm
Regarding best practice for password complexity: it depends on whether it's only used only for authentication (ie: Netflix) - or if it's leveraged for symmetric key encryption and there is a chance the hacker can acquire the raw encrypted data (ie: an encrypted .zip file that you email to your tax accountant). Of course, your email password - just like your banking or Google password - needs to be complex and unique because it can be a side door into numerous other accounts.
"Do not seek to follow in the footsteps of the wise. Instead, seek what they sought." - Matsuo Basho
-
March 29, 2022 at 2:19 pm
david.edwards 76768 wrote:I like that chart Jeff, I might add it to my favourite argument I trot out every time I am faced with a short password requirement that forces numbers, capitals etc.
I am sure everyone is aware of it, the "Correct Horse Battery Staple" XKCD cartoon, but if not...
Should point out, I usually add a Latin word to help mitigate dictionary attacks and where I am constrained capitalise etc.
I'm thinking a there could be a theoretical AI algorithm capable of matching and prioritizing combinations of related words to greatly improve the efficiency of a dictionary attack.
"Do not seek to follow in the footsteps of the wise. Instead, seek what they sought." - Matsuo Basho
Viewing 15 posts - 1 through 15 (of 16 total)
You must be logged in to reply to this topic. Login to reply