Securing SQL Server Database is a challenging task as there are number of external and internal risks or parameters affecting the Server and its databases. In this section, we have discussed about all the concepts and the precautions that can be taken to prevent databases and the accumulated components such as tables, stored procedures, triggers, etc. To protect the SQL DB, it is mandatory to provide security to the overall SQL infrastructure. Therefore, this approach is divided into given segments;
- Platform Security
- Application Security
- Database Security
Let’s discuss about these parameters in detail, so as to get better understanding on all the perspectives that can help safeguard crucial information existing under SQL environment.
Platform Security:
Platform security of the database refers to securing the hardware components from outside risks. It can be done by proposing access limitations for SQL Server to the few and authorizing users. It is recommended to store the backup media at some offsite location with secure and minimal access. This can be done by configuring least users with access authorities and controlling unauthorized access on network devices and components.
The integral components such as Operating System and associated files can be protected by referring to the below mentioned measures;
Method 1:
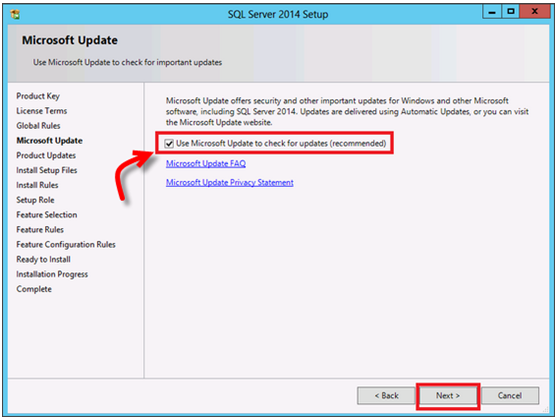
Update Notifications:The internal security of the SQL Server Operating System can be ensured by installing genuine applications. After installing any new application or software in SQL Server, do always remember to update the associated notifications and security enhancements received from Microsoft.
Note:This can alternatively be done while installing SQL Server 2014 by checking the associated checkbox in the set-up window.
Method 2:
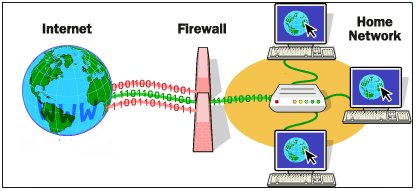
Keep Firewalls On: By keeping the Firewalls On, the security measures can be increased to ensure extended security. Firewalls are considered the security system that controls the network traffic by applying defined set of rules. It serves as the barrier between secure network (such as home network) and the external network such as internet (that might not be secure or fully trusted).
Application Security:
Since SQL Server relies upon systems’ files in order to store data components so it is important to limit the access to these files for assuring more data security. This can be done by implementing the following given methods;
Method 1:
Access Authority: By assigning access restrictions to the distinct users existing on database, the files can be prevented from any unauthorized access. By doing so, the files can only be accessed by the users who are marked eligible to access them by the Database Administrator.
Method 2:
Authentication Check: Another powerful method to protect the integrity and security of data is via assigning strong passwords to the important files. This method can be implemented in a powerful manner when used with the combination of access authorities.
Database Security
Now the most powerful aspects comes i.e. the SQL Database and the incorporated objects such as data stored in tables, stored procedures, indexes, triggers and all other components. Following concepts can be utilized for securing SQL Server and the data components from all sorts of internal and external factors.
Method 1:
Regular Backup: It is recommended and even serves as a best practice to backup SQL database and system log files on regular basis so as to avoid any data loss. Backup approach provides full security over data as if entire database or any of its components becomes inaccessible due to corruption or any other reason, the lost data can be gained back via backup restoration.
Note:Sometimes user forget to take regular backup or scheduled backup.In that case, if any database corruption occur or any accidental deletion of data occur, the chances of data loss becomes quite high. So in that case, you can use SQL Database Recovery Software for repairing and recovering of your SQL Server Database.
Method 2:
Data Encryption: The most powerful way to safeguard data and all encapsulated elements is via encrypting the files or the segments of data. However, this approach will not help in controlling the access over database but in case if the crucial information is leaked out via any unknown resources; it will not put any adverse effect on the data or the concerned person (to whom the particular information belongs to).
Conclusion:
Since the information existing into SQL databases is crucial as it includes data associated to many users or individuals. It is important to protect it from unauthorized access and illegal interruptions so as to avoid the occurrence of adverse circumstances. Using either or all of the above stated tips to secure SQL Server Database, the entire infrastructure, the application or the encapsulated data can be protected from distinct kinds of risks factors.