Last week I wrote a blog post about Decoding Helm Secrets.
The post goes through deploying a Helm Chart to Kubernetes and then running the following to decode the secrets that Helm creates in order for it to be able to rollback a release: –
kubectl get secret sh.helm.release.v1.testchart.v1 -o jsonpath="{ .data.release }" | base64 -d | base64 -d | gunzip -c | jq '.chart.templates[].data' | tr -d '"' | base64 -d
But that’s a bit long winded eh? I don’t really fancy typing that every time I want to have a look at those secrets. So I’ve created a kubectl plugin that’ll do it for us!
Here’s the code: –
#!/bin/bash
# get helm secrets from Kubernetes cluster
SECRET=$(kubectl get secret $1 -o jsonpath='{ .data.release }' )
# decode the secrets
DECODED_SECRET=$(echo $SECRET | base64 -d | base64 -d | gunzip -c )
# parse the decoded secrets, pulling out the templates and removing whitespace
DATA=$(echo $DECODED_SECRET | jq '.chart.templates[]' | tr -d '[:space:]' )
# assign each entry in templates to an array
ARRAY=($(echo $DATA | tr '} {' 'n'))
# loop through each entry in the array
for i in "${ARRAY[@]}"
do
# splitting name and data into separate items in another array
ITEMS=($(echo $i | tr ',' 'n'))
# parsing the name field
echo "${ITEMS[0]}" | sed -e 's/name/""/g; s/templates/""/g' | tr -d '/:"'
# decoding and parsing the data field
echo "${ITEMS[1]}" | sed -e 's/data/""/g' | tr -d '":' | base64 -d
# adding a blank line at the end
echo ''
done
It’s up in Github as a Gist but to use the plugin, pull it down with curl and drop it into a file in your PATH environment variable. Here I’m dropping it into /usr/local/bin: –
curl https://gist.githubusercontent.com/dbafromthecold/fdd1bd8b7e921075d3d37fcb8eb9a025/raw/afa873b0ef343859ed4119eeb9f41bf733e8cea2/DecodeHelmSecrets.sh > /usr/local/bin/kubectl-decodehelm
Make it executable: –
chmod +x /usr/local/bin/kubectl-decodehelm
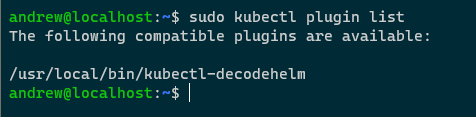
Now confirm that the plugin is there: –
sudo kubectl plugin list
N.B. – I’m running this with sudo as I’m in WSL which will error out when checking my Windows paths if I don’t use sudo
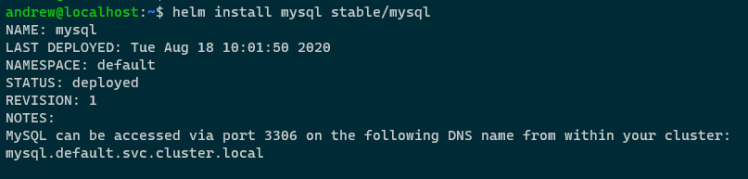
Let’s test it out! I’m going to deploy the mysql chart from the stable repository: –
helm install mysql stable/mysql
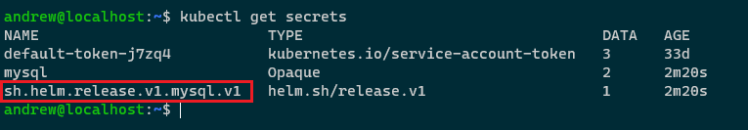
Once deployed, we’ll have one secret created by Helm: –
kubectl get secrets
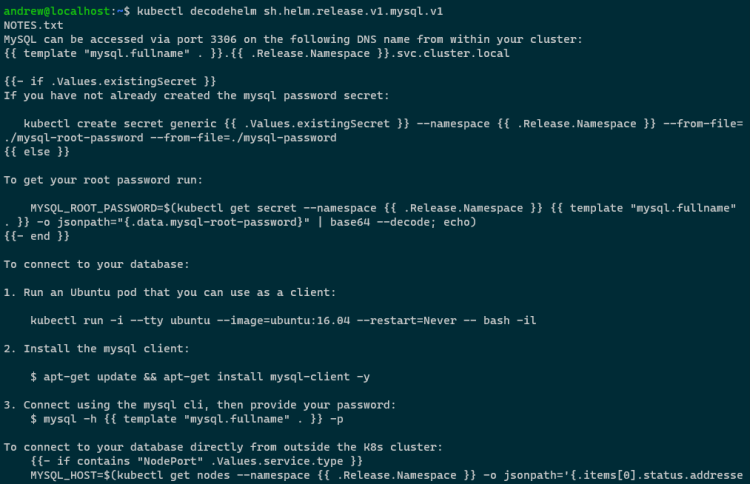
Now let’s use the plugin to decode the information in that secret: –
kubectl decodehelm sh.helm.release.v1.mysql.v1
And there’s the decoded secret! Well, just a sample of it in that screenshot as the mysql Chart contains a few yaml files.
The format of the output is: –
- Filename (in the above example… NOTES.txt
- Decoded file (so we’re seeing the text in the notes file for the mysql Chart)
Thanks for reading!