SQLServerCentral.com Rating:
Introduction
NGSSquirrel is a SQL Server security scanner from Next Generation Software (NGS,
website: http://www.ngssoftware.com). The
NGSSquirrel application is designed to perform comprehensive security evaluations of
SQL Server instances and report on the threats and vulnerabilities it locates.
NGS also offers NGSSquirrel versions specific to the Oracle, Informix, Sybase, and
DB2 platforms, but this review focuses on the SQL Server version.
Environment
Although a network is not required (NGSSquirrel can be run on a standalone SQL Server), I
tested it in a networked environment on six individual SQL Server instances installed on
two machines. NGSSquirrel has the following minimum system requirements:
- Pentium III or Athlon (1 GHz) processor
- 256MB RAM minimum
- Windows NT 4.0 (SP 4)/XP/2000/2003
- 20 MB HDD Space free
For this review I tested NGSSquirrel on two hosts with the following configurations:
| Host 1 | Host 2 | |
| Processor: | AMD Athlon 64 Processor 3500+ | AMD Turion 64 X2 (1.6 GHz) |
| Operating System: | Windows XP Professional SP 2 | Windows XP Media Center Edition SP 2 |
| Memory: | 2 GB RAM | 2 GB RAM |
| SQL Server: | SQL Server 2000 SP 4 default instance SQL Server 2005 SP 1 named instance SQL Server Express (2005) SP 1 named instance | SQL Server 2005 SP 1 default instance SQL Server 2000 SP 4 named instance SQL Server Express (2005) SP 1 named instance |
Installation
The NGSSquirrel installation is a standard InstallShield package making the whole process
quick and easy. It took me about 5 pain-free minutes to install. Figure 1 below shows the
first screen of the NGSSquirrel installation.
Figure 1. NGSSquirrel installation screen
The first time I ran NGSSquirrel it asked me to enter my username and email address. I
requested an activation key over the Internet, and it was promptly delivered to me via
email. Figure 2 below shows the license key request window. After copying and pasting
the activation key into the NGSSquirrel activation window, I was ready to configure the
program to scan my SQL Server instances.
Figure 2. NGSSquirrel license key request window
Registering Hosts
Once NGSSquirrel is installed and activated the process of registering hosts in
the application begins. I registered two hosts (physical computers) with the application
during testing. One was the local computer NGSSquirrel was running on; the other was the
remote laptop. Figure 3 below shows the Add Hosts window.
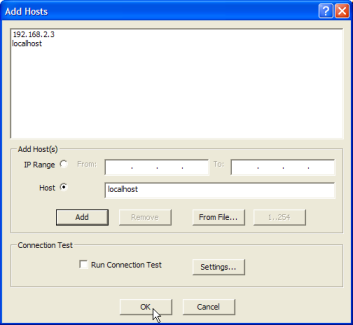
Figure 3. Add Hosts window
I did encounter a couple of minor inconveniences while registering hosts with
NGSSQuirrel. The first was that I could not register specific SQL Server instances
directly from the Add Hosts window. The backslash character, required for named instances
in the form "MyServer\MyInstance" is not allowed in the Add Host window.
NGSSquirrel separates host (physical computer) and instance (SQL Server instance)
registration into two steps. The Add Hosts window is strictly for adding host computer
names and IP Addresses. You have to then add SQL Server instances in a second step. This
process might be a little less intuitive for those of us who are used to registering SQL
Server instances with programs like Enterprise Manager or SQL 2005 SSMS, but NGS does
document the procedure.
The second minor issue was when I tried to register my local host as "(local)",
which is fairly standard practice. Unfortunately I couldn't register any SQL Server
instances with a host name of "(local)". This was remedied easily enough,
however, by registering the local host using the name "localhost" instead (see
Figure 3).
Adding SQL Server Instances
After I added my two hosts, the next step was to add the SQL Server instances to
NGSSquirrel. NGSSquirrel automatically enumerated all of the SQL Server instances on
"localhost" and on the remote host after I turned on the SQL Server Browser
service. Figure 4 shows the instances automatically registered with localhost.
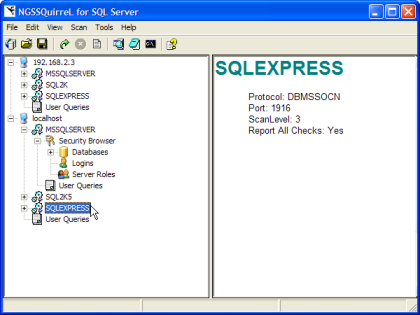
Figure 4. NGSSquirrel registered hosts
If for some reason NGSSquirrel can't automatically register your SQL Server instances
(if the SQL Server Browser service is turned off, for instance), you can manually add
instances by right-clicking on the host and choosing Add/Remove Instance from the pop-up
menu. The Add Instance window is shown in Figure 5.
Figure 5. Adding an instance to NGSSquirrel
After manually registering SQL Server instances I had to specify authentication
settings and connection settings on a per-instance basis. To do this I right-clicked
the instance name and chose Scan Settings to bring up the Scan Settings window
to set the authentication credentials, connection settings (like port number and
protocol), and reporting options. The Scan Settings window is shown in Figure 6.
Figure 6. Scan Settings window
The NGS team spared no expense in packing NGSSquirrel full of options and additional
features. This is a common theme throughout the application. NGSSquirrel is an extremely
flexible and powerful application; though taking it all in can be a bit much in just one
sitting. Fortunately the NGS team included a Quick Start guide in the documentation that
can get you up and running in a matter of minutes.
Ready... Set... Scan!
Once I registered the hosts and SQL Server instances with NGSSquirrel, it was time to
put the program through its paces. I ran several scans against all my SQL Server
instances. To scan, I just highlighted the instance name and selected Scan This Instance
from the menu. Each scan was completed in a matter of minutes, and I must say NGSSquirrel
does a very thorough job.
Some of the items NGSSquirrel reported back were expected: some of my test account
passwords were extremely simple, I have xp_cmdshell activated on a couple of instances,
and a couple of my test accounts have excessive rights to various parts of the server. I
already knew about these items, and expected NGSSquirrel to report them.
But then something really impressive happened: NGSSquirrel found dozens of security
issues I didn't expect, and it found them extremely quickly. Some of the additional items
NGSSquirrel found included:
- old test accounts I hadn't used in months (and had completely forgotten about),
- several potentially dangerous extended procedures above and beyond xp_cmdshell,
- various SQL setup files that had been left lying around on my hard drive which
could conceivably contain passwords
In addition, NGSSquirrel can automatically perform simple password checks (like
blank password and password same as username), and it can even detect Trojan software
like the Spida worm and CBLADE worms.
For every issue NGSSquirrel uncovered, it gave a very thorough description of the
problem, as well as suggestions for fixing it. In many cases T-SQL statements were
provided to copy and paste over to Query Analyzer or SSMS to fix the issue immediately.
The NGS team did a great job of describing the various issues NGSSquirrel detects. The
level of detail makes it very easy to perform additional research on your own if, like
me, NGSSquirrel reports some issues you would like to investigate further before making
the recommended changes.
The Reports
If there's one area that separates NGSSquirrel from the competition, it's reporting.
NGSSquirrel not only generates highly detailed reports, it can generate them in a wide
variety of formats including HTML, Dynamic HTML, XML, Plain Text, and even Rich Text
Format (RTF). You can even export the report information to a SQL Server table via
ODBC, a potentially useful feature for enterprise-wide reporting when dozens (or even
hundreds) of SQL Server instances are being audited.
The level of detail reported by NGSSquirrel is outstanding. The issue descriptions are
thoughtful, easy to read, and many contain references to external sources of information as
well as recommended fixes. After I scanned my SQL Server instances, I used NGSSquirrel's
Generate Lockdown Script(s) option to automatically create T-SQL scripts to fix the
problems.
Figures 7, 8, and 9 show the Export Report menu options, a sample NGSSquirrel report
summary, and an NGSSquirrel report exported to a SQL Server table, respectively.
Figure 7. Export Report options
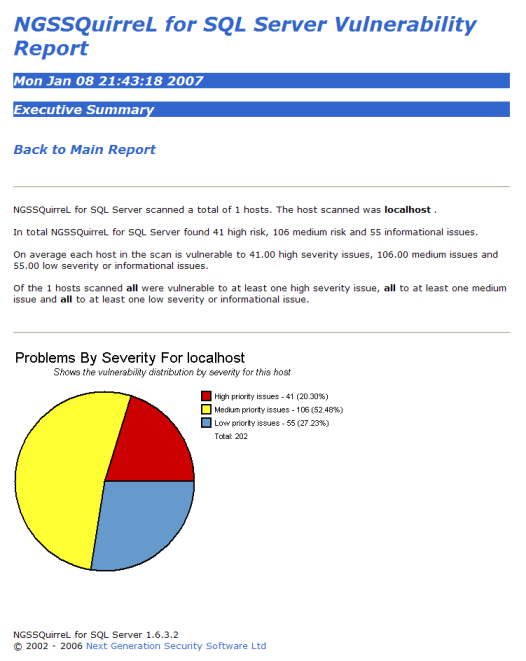
Figure 8. HTML Summary Report
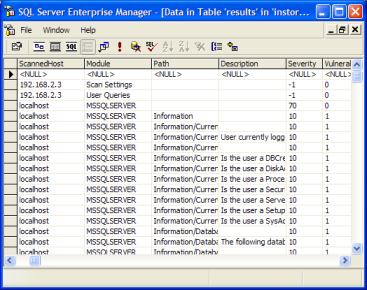
Figure 9. Report exported via ODBC
The Bonus: SQLCrack Password Auditing
SQLCrack is NGS' SQL Server password checking tool. It can be purchased as a
stand-alone password audit utility, but NGS has upped the ante by including it free with
NGSSquirrel. The installation and registration for SQLCrack are similar to NGSSquirrel.
SQLCrack does, however, require its own license key (separate from NGSSquirrel's license
key). Like NGSSquirrel, the license key can be requested online and is sent to you by
email.
SQLCrack can perform several types of password checks, including:
- Blank password checks
- Checks for passwords that are the same as the username
- Dictionary attacks with pre-defined prefixes, suffixes, backwards words, and common
number-for-letter substitutions (like "3" for "E"). SQLCrack comes
with a sample dictionary of nearly 27,000 words, although you can use your own
dictionary
- SQLCrack can also perform brute force attacks with a character set and minimum and
maximum password lengths that are fully customizable
Figure 10 shows the SQLCrack password crack settings window.
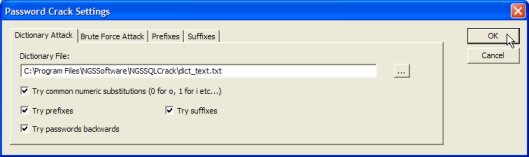
Figure 10. SQLCrack password crack settings
I performed brute force and dictionary attacks on a couple of my SQL Server instances
and found some of the passwords were extremely lax. The brute force attack took several
minutes on my computer to finish using one of the pre-defined character sets and checking
for passwords between 8 and 12 characters in length. That is entirely understandable
though, since the number of permutations checked was 12,381,557,518,345,418,442.
Figure 11 shows the SQLCrack brute force attack in progress.
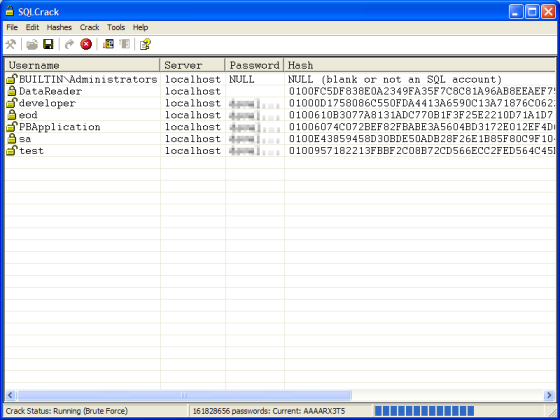
Figure 11. SQLCrack brute force cracking in progress
First Impressions
I was extremely impressed by the power and flexibility of both NGSSquirrel and SQLCrack.
Once you register the SQL Server instances and start the process, it runs smoothly to the
end.
The reports NGSSquirrel generates are well-designed and formatted for easy reading. The
descriptions of issues NGSSquirrel locates and the suggested fixes are well-written and
thorough. The fact that you can dump your reports directly into a SQL Server table should
make enterprise-wide SQL Server auditing, comparisons, and report generation much easier.
Conclusions
Overall I found NGSSquirrel's power, flexibility, and speed impressive. The report
generation features rate an A+, and the documentation is complete and accurate. If there
is one improvement that could make NGSSquirrel even better, it would be to make the user
interface more intuitive. Some of the menu items weren't where I would normally expect
them to be, and some just required some testing to determine how they worked. A simple
wizard for basic scanning would definitely make it easier for casual users to jump right
in and run basic scans against a single host or SQL Server instance. It took me one
sitting to locate and test all of the options I felt I needed, but by the second use I was
fairly proficient in the NGSSquirrel menuing system.
[Editors Note: NGS is considering adding a wizard interface in a
future version of the product]
I highly recommend these products for auditing production and development SQL Server
instances on a regular basis. In development environments in particular, accounts are
created, rights are assigned, and new objects are added far more often than in a production
environment. In the development environment, security is often a secondary consideration.
Regularly scanning your development servers with NGSSquirrel can help keep your development
environment from being compromised. This is particularly important if a hacker could potentially
gain access to other critical systems from within your development environment.
Ratings
Here are the summarized ratings I gave these products:
| Category | Rating | Comments |
| Ease of Use | 3 | The sheer volume of customizations and options, the fact that adding SQL Server instances manually is a two-step process (add host/add instance), and some of the less intuitive menu options provide a slight learning curve at first. |
| Feature Set | 5 | There are customization options for nearly everything in these applications, making them a couple of the most flexible security auditing applications I've encountered. |
| Lack of Bugs | 5 | No major issues encountered. |
| Value | 5 | NGSSquirrel is an excellent security auditing product, and the included copy of SQLCrack definitely sweetens the pot. |
| Technical Support | 5 | NGS technical support was very responsive and provided immediate feedback to all my questions. |
| Documentation | 4 | The online documentation includes everything you need to get up and running, with a complete reference to all customizable options. |
| Performance | 5 | NGSSquirrel is very fast and very thorough; an excellent combination. |
| Installation | 4 | InstallShield install: easy, quick, and no unexpected surprises. The license key/registration process was a little different, but the turnaround time was very fast. |
| Learning Curve | 4 | The first time you sit down with NGSSquirrel, prepare to perform a couple of test scans. The menuing system takes a little bit of getting used to, and you will probably need to play with the customizable options to determine the right combination for you. The second go-round you'll be running it like a pro. |
SQLServerCentral.com Rating:
Product Information
NGSSquirrel and SQLCrack are available from Next Generation Software.
Next Generation Software
Email: sales@ngssoftware.com
Website: http://www.ngssoftware.com
©2007 by Michael Coles, author of the upcoming Apress book Pro T-SQL 2005 Programmer's Guide (April 2007). |


