Introduction
MuleSoft Anypoint is a platform that helps to aggregate and integrate data from different source systems. As part of the data integration, the MuleSoft Anypoint Environment needs source system and target system login credentials stored in the platform, making it a vulnerability.
The storage is vulnerable to attacks from cyber-criminals. This vulnerability can arise from the hardware, software, or other linked channels. Therefore, organizations are concerned about storing this sensitive information at the local application layer. If the security of these credentials is compromised, the organization may face detrimental consequences such as financial lawsuits, ransom attacks, and loss of customer trust. The gravity of this issue can range from strained local organizational affairs to relationships between multinational organizations.
To prevent the above scenarios, organizational cyber security specialists have developed various policies and procedures that fundamentally comprise two principles:
- removing sensitive credentials from the application layer and storing them in isolated security services such as cloud secret manager (Azure Key Vault)
- auto-rotating passwords periodically.
Azure Key Vault’s Properties
Azure Key Vault (AKV) is a cloud service for securely storing and accessing secrets. A secret is anything that needs tight control access, such as API keys, passwords, certificates, or cryptographic keys.
The Current System:
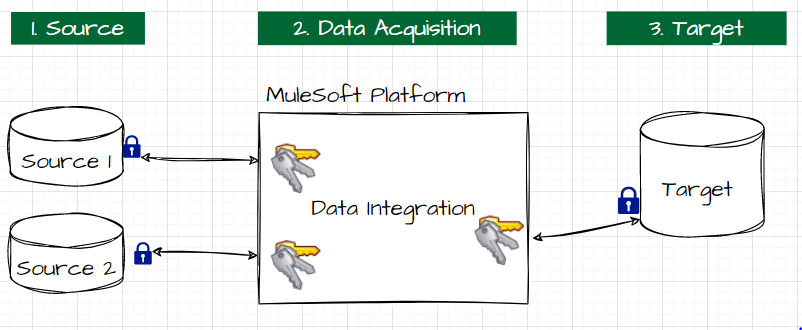
The Desired System:
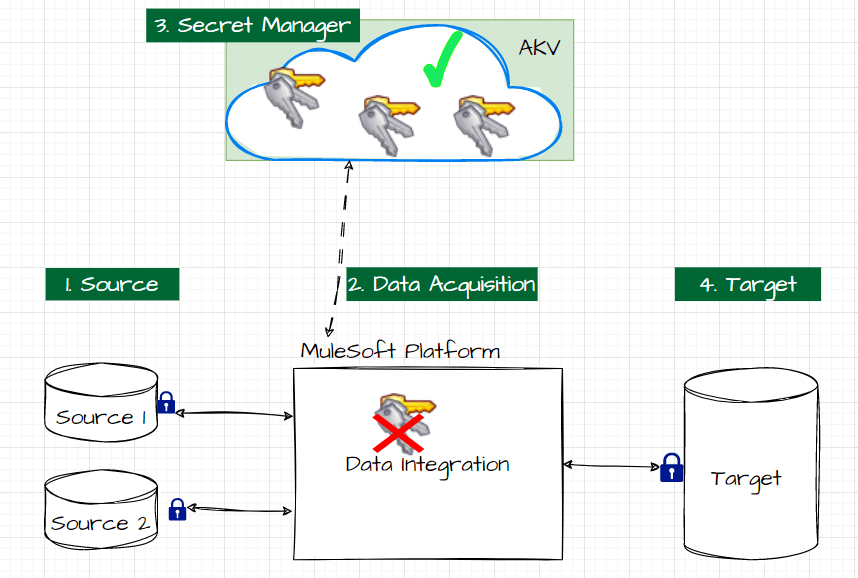
As mentioned, the secret credentials can be secured by moving them to a secret manager service such as AKV. To fetch these secrets from AKV, two types of connectors are being facilitated by MuleSoft Anypoint; they are:
- Azure Key Vault Properties Provider
- Azure Key Vault Connector.
To integrate MuleSoft Anypoint data into Azure Key Vault, the second connector (Azure Key Vault Connector) will be primarily used. The key difference between these two connectors is whether the secrets are manually or automatically rotated. Below is a brief comparison of the two connectors.
| AKV Properties Provider | AKV Connector | |
| This connector is used when the secrets must be rotated manually. This connector retrieves secrets before runtime activation, enabling it to fetch secrets from Azure Key Vault and authenticate to connectors before the Mule app executes.
| This connector is used when the secrets must be rotated automatically. This connector makes compliance easier with key rotation and version control for secrets. It uses key and password versions in the connector to automatically rotate secrets for authenticating applications. |
Since our objective is to automate the rotation of the secrets (passwords), we will use the second AKV connector from the MuleSoft Anypoint Platform.
Azure Key Vault Implementation
In this section, I will walk through the steps to implement Azure Key Vault. There will be a detailed explanation of each step and images associated with it as well to help navigate the implementation.
POM.XML File
In the MuleSoft project, the pom.xml file contains the core information about a project and its configuration details, dependencies, build directory, source directory, test source directory, plugin, and goals.
To Integrate the MuleSoft project with AKV, we need to add the below dependency to the pom.xml file to make the AKV connector available for the MuleSoft Platform.
<dependency> <groupId>com.mulesoft.connectors</groupId> <artifactId>mule4-azure-keyvault-connector</artifactId> <version>1.0.1</version> <classifier>mule-plugin</classifier> </dependency>
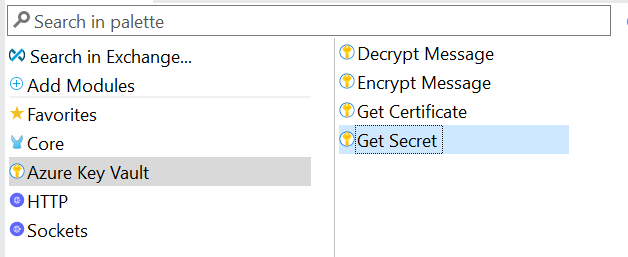
Mule Palette
Open the MuleSoft palette and search for Azure Key Vault. The Azure Key Vault has different functions within it.
MuleSoft AKV Connector configuration
Open the Mule App and search for “Global Elements.” Click on Global Elements and then click on “Create.” Once that is done, choose Connector Configuration.
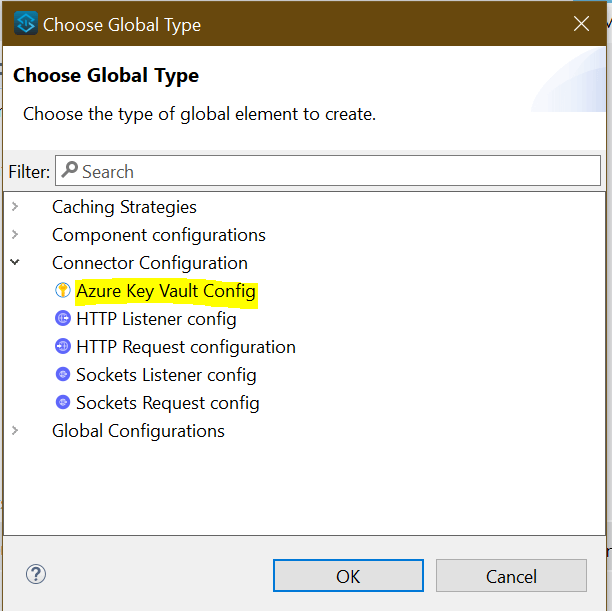
Azure Key Vault Configuration Setup
There will be an “Azure Key Vault Configuration within Connector Configuration.” Press on this and this will then open a pop-up, as shown below.
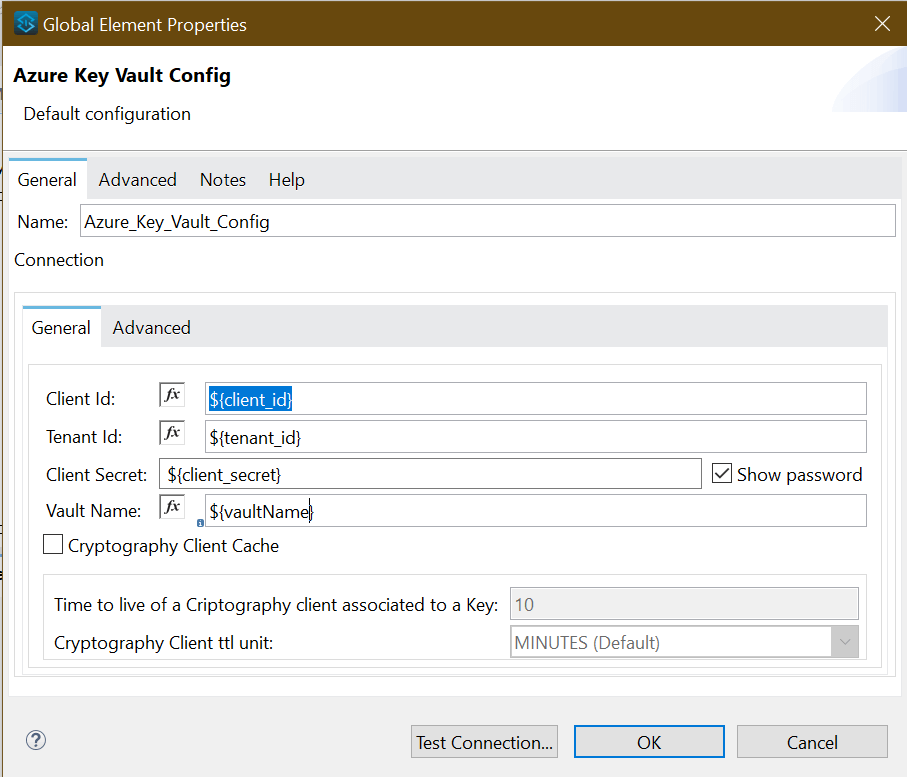
Supplying values from each environment
Provide the application's Client Id, Tenant Id, Client Secret, and Vault name to be integrated. Replace all the values while running it locally, as shown below.
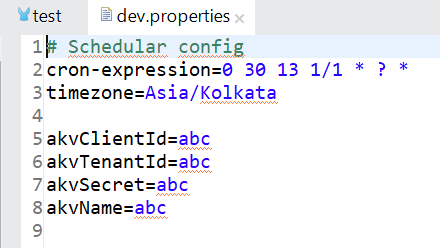
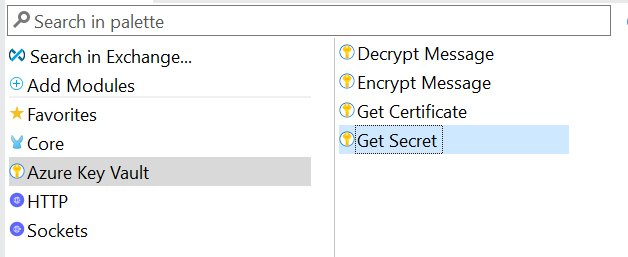
Get Secret Method
Use the “Get Secret” function to fetch the secrets from Azure Key Vault. Azure Key Vault provides the following four methods to perform various functions. Each function has unique properties. Below is a description of what each function encompasses.
- Get Secret - Retrieves runtime passwords for a database or HTTP connectors
- Get Certificate - Retrieves certificates to use in a TLS context
- Encrypt Message - Has Azure Key Vault encrypt message contents
- Decrypt Message - Decrypts message content to use in Mule flows
Summary
The major takeaways from this article are:
- Credentials stored in MuleSoft are in the application layer and, therefore, can be more secured by moving to a secret manager service such as Azure Key Vault
- MuleSoft has two types of connectors to Azure Key Vault (1. Azure Key Vault Properties Provider and 2. Azure Key Vault Connector), each with different features.
- Azure Key Vault Connector automates the rotation of secrets such as passwords in Azure Key Vault.
References
- Azure key vault properties provider documentation - https://www.mulesoft.com/exchange/com.mulesoft.module/mule4-azure-key-vault-properties-provider/
- Azure Key Vault Connector - https://www.mulesoft.com/exchange/com.mulesoft.connectors/mule4-azure-keyvault-connector
- Protecting App Properties in Cloudhub 2.0 - https://docs.mulesoft.com/cloudhub-2/ch2-protect-app-props#:~:text=CloudHub%202.0%20enables%20you%20to,the%20property%20internally%20at%20runtime.



