Linked server - Cross domain - Windows authentication only.
-
May 8, 2019 at 11:22 am
Hi all,
I was looking for some advice on the best way to do this, we have our domain (A) and a parent companies domain (B).
For a long time now one of our applications running in our domain has been using a linked server also in domain A to get data from domain B - This was done using SQL authentication.
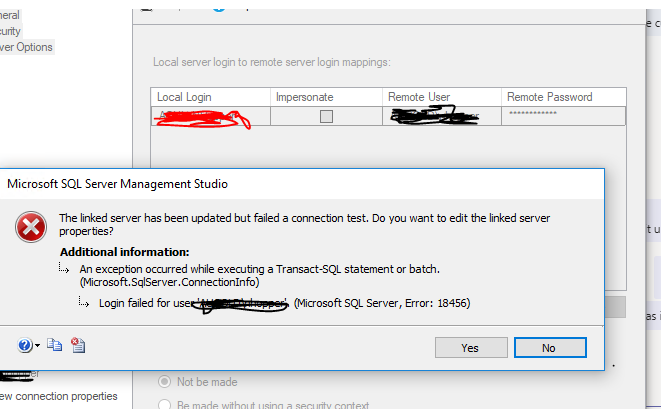
Now however they have made changes and require us to use a Windows account but I'm not sure how to go about this, I've tried some impersonation settings on the linked server (see image, black is domain B detail, Red is domain A).

The error on the server on domain B is
Login failed for user 'DomainB\User'. Reason: Attempting to use an NT account name with SQL Server Authentication. [CLIENT: 123.123.123.123]
Does anyone have an ideas on how to achieve this?
Thanks,
Nic
-
May 8, 2019 at 11:57 am
Did this year's ago, it was way back and what was required was to set up cross domain trusts such that one domain was trusted and the other trusting.
...
-
May 8, 2019 at 3:11 pm
Hi,
Thanks for the reply and when that is done (the trusting) will what I did work? Or do I need to do something else?
Thanks,
Nic
-
May 8, 2019 at 3:29 pm
Granted that your DNS is clean .. and has forwarders and your spns are correct, it should work once the domains have trust.
-
May 8, 2019 at 3:50 pm
I think you'll need to reconfigure your linked server object as well. The error message suggests that you are trying to force Windows credentials where it's expecting a SQL login. I can't remember exactly how you do it, but it may involve ticking the Impersonate box. Oh, and make sure you've got all the SPNs you need in place in order to make Kerberos work, or you'll suffer from the double-hop problem.
John
-
May 8, 2019 at 4:39 pm
John Mitchell-245523 wrote:I think you'll need to reconfigure your linked server object as well. The error message suggests that you are trying to force Windows credentials where it's expecting a SQL login. I can't remember exactly how you do it, but it may involve ticking the Impersonate box. Oh, and make sure you've got all the SPNs you need in place in order to make Kerberos work, or you'll suffer from the double-hop problem. John
Yup. You can't specify a windows account as the remote account when setting it up like the screenshot. You need to specify Impersonation, don't put in a remote login and password.
Sue
-
May 9, 2019 at 1:54 pm
Also, be aware that if you granted access to an AD group from another domain (despite trusts are in place), such AD group should be either Universal or Global type. Otherwise, your AD account (member of AD group) will not be authenticated.
To check that use xp_logininfo command in the following way on the target server:
exec xp_logininfo 'anotherdomain\ad_group','members'
If this returns nothing, it means that SQL server can't get members of the group and your account will not be authenticated.
I had such issue twice in the past and it was rather hard investigation.
Viewing 7 posts - 1 through 7 (of 7 total)
You must be logged in to reply to this topic. Login to reply