Introduction
Typhon III is a general security scanner from Next Generation Software.
Unlike specialized tools like NGSSquirrel (for Oracle or SQL Server), Typhon III
doesn't concentrate on any one product. Rather, it is designed for an
administrator scanning his or her entire network for vulnerabilities on a mix of
systems. Other tools in the same class include GFI Languard and Nessus.
Typhon III is designed to be as minimally intrusive as possible; it does not
scan in a manner that could result in a system's denial of service (DoS) or
eating up too many resources. Instead, Typhon III looks for tell-tale signs of
issues without performing the attack such as missing or incorrect registry
entries or parsing banners and the like. If you are familiar with Nessus, it
functions similar to how Nessus does when Nessus is configured to scan using
"safe checks" only: parsing the text that comes back from a connection
is how the vulnerability is diagnosed rather than actually carrying out the
exploit.
Environment
Typhon III is a standard Windows application designed to run on Windows NT
4.0 and up. It requires a minimum of 128 MB of RAM and a Pentium III as the
platform. If you're running on the Windows NT 4.0 platform, the system must have
service pack 6a as well as the Active Directory Client extensions (which are
included with Windows 2000 and Windows XP).
Installation
Installation of the product was smooth and without issue as Typhon III uses a
standard InstallShield installer. However, Typhon III does require a few additional steps in order to get the product up and running. The first step is to
generate a license key request. The license key request is therefore tied to the
system on which Typhon III is installed. Next you forward this license key request to Next Generation Software. If you've gone through the process of
receiving an SSL server certificate from GeoTrust, Thawte, VeriSign, or
other certificate authority, it's much the same. Then, Next Generation Software responds with a license block which enables the application. Finally,
you install the license block and activate the software.
Using Typhon III
If you've never used Typhon III before (or any security scanner, for that
matter), not to worry. Typhon III starts up with the set of instructions to get
you started in the right pane (Figure 1). But like most security products,
before starting with step 1 you should always check for patch updates (Tools |
Update Patch Checking File).
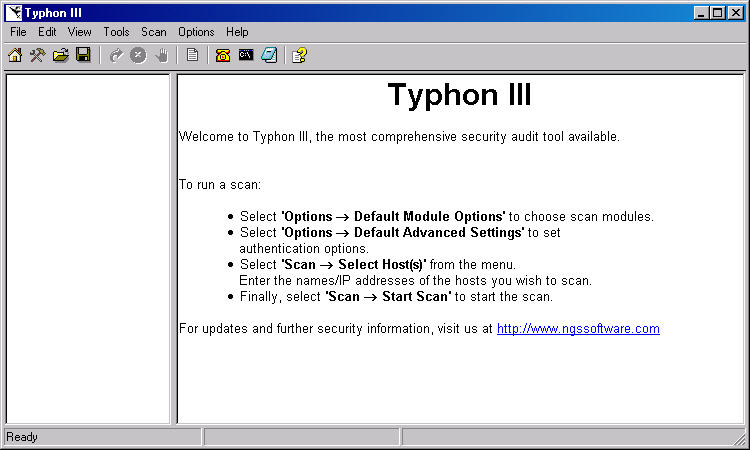
Figure 1: Typhon III Start-up
The first step when beginning a scan with Typhon III is to set the module
options (Options | Default Module Options or Options | Host Module Options).
Figure 2 shows a sample set of options I selected to scan my local system. I
have removed some of the options because I know they aren't present on the
system I decided to run the scan against. For instance, the system doesn't have
an SMTP server nor does it have an X-Windows server installed
and running. If you aren't sure, don't worry. Typhon III can detect whether or
not it needs to run a given module on an individual system if you've checked the
option to include the module. Therefore, if you're uncertain about an option,
check it.
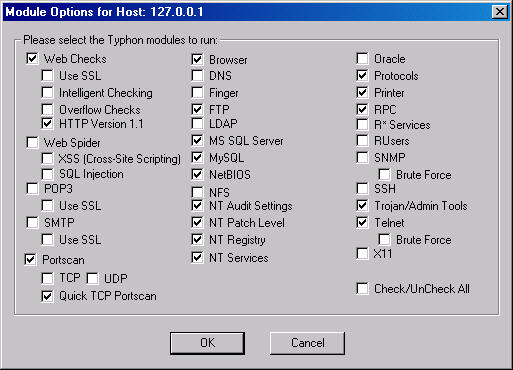
Figure 2: Module Options
The next step is to select any advanced settings that may be necessary for
the scan (Options | Default Advanced Settings or Options | Host Advanced
Settings). For instance, if you need to specify a different username and
password combination in order to scan systems on your network with your
administrative account, you'd do so here. Since I logged on as a privileged user
to test Typhon III, I selected to run the scan using the current credentials
(Figure 3). Also, I chose to only report problems though Typhon III can report
all the tests it's running and the results of those tests, if you'd like.
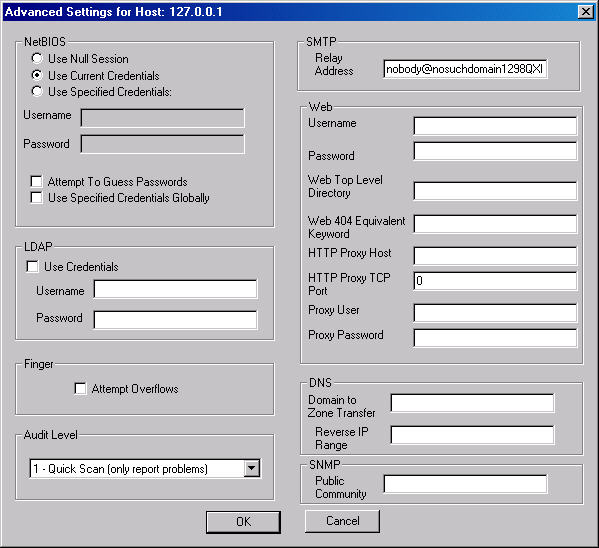
Figure 3: Advanced Options
The last thing to do before beginning a scan is to set the host(s) to be
scanned (Scan | Select Select Host(s)...). In my case I only selected the local
system (Figure 4) though you can add multiple systems individually or specify a
range of IP addresses.
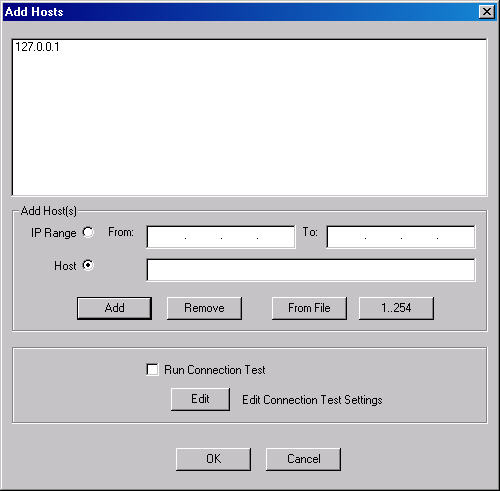
Figure 4: Selecting What to Scan
Here is where I found the only glitch in the program. You can specify
hostnames rather than IP addresses and generally this works. If I have a host
named "Brian" Typhon III adds it just fine. However, if there is a
dash in the name (a perfectly legal character in names), Typhon III returns an
error (Figure 5) indicating only alphanumeric characters are allowed. That means
"Brian" is legal, but "Brian-SQL" is not.
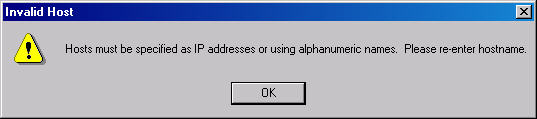
Figure 5: Error when Specifying a Name with a Dash
Update from the Editor: Upon being informed of this bug from the review, NGS Software notified us that it had been corrected within 24 hours.
Brian used the application to download the update and the issue was corrected.
With everything configured, the only thing left to do is run the scan (Scan |
Start Scan). Typhon III reports findings as it performs the scan or you can wait
until Typhon III completes (Figure 6). It does a good job of categorizing the
potential vulnerabilities and the icons convey the severity of what it has found
at a glance. Explanations are given for each vulnerability if you're not sure of
what the issue is. Also, Typhon III usually gives a recommendation, if one is
available, on a good control or setting should the "vulnerability" be
related to a configuration setting rather than due to a bug.
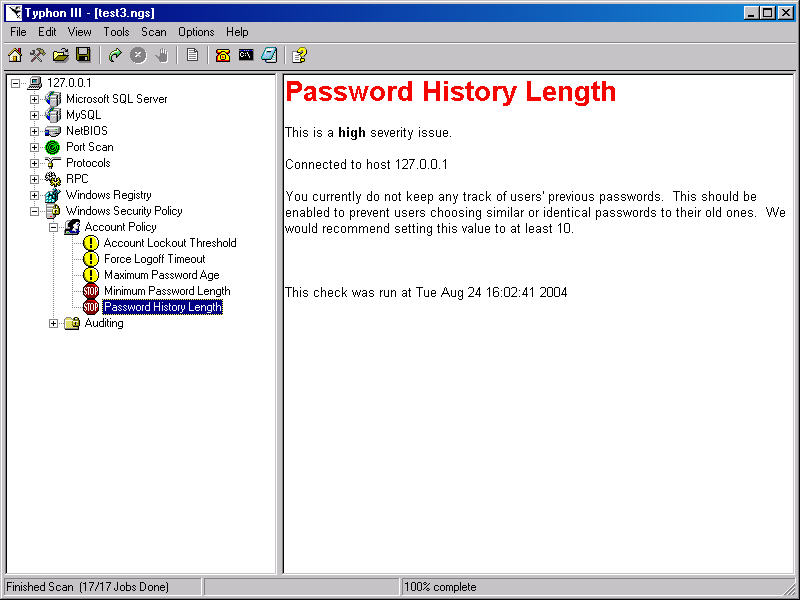
Figure 6: Vulnerability or Issue Found
First Impressions
The first thing that struck me about Typhon III was how easy it was to get
the scanner up and running. For an administrator, getting the scan setup and
running takes very little time at all. For someone who is new to security or
whose job functions mean little time can be dedicated to that endeavor, Typhon
III is easy to use and simple to understand.
Most of the time I use Nessus and while Nessus is fairly quick to get up and
running, configuring it to really do what you want can take some time.
Vulnerabilities are grouped together like in Typhon III but the list can be
quite intimidating for someone who hasn't used Nessus before. Also, if
you're not careful with Nessus, you can take a system down if it's not properly
secured and up-to-date on all security patches. Having witnessed another
well-trained security administrator crash a system, it's nice not to have to
worry about this with Typhon III. In that security administrator's defense, we
had both been working 60 hour weeks trying to get an application out the door
and in his exhaustion he typed a 1 instead of a 2 when specifying the system to
scan. But that does illustrate why you may want the safety in Typhon III.
No scanning tool is very useful without reporting. Typhon III does well in
this regard. Generating reports was easy and you have the option of several
formats, including dumping the results straight to an ODBC data source. The
reports are clean and easy to read.
Conclusions
Overall I was favorably impressed with Typhon III. It's quick and easy... and
safe. Also, it does a good job explaining the vulnerability or issue when it
finds one and this is a great help. Quite simply, with so many security
vulnerabilities and exploits coming out each week, it's hard to keep track. And
Typhon III is pretty detailed and in-depth. For instance, it can go in and check
databases and database roles within SQL Server. Nessus, for instance, isn't
capable of this out of the box (and it's not something that would be
straight-forward and easy to do with Nessus, either).
There are two things I didn't like about Typhon III. The first is that you're completely
dependent upon Next Generation Software for updates. Unless you're interested in
writing your own scans, though, this is a non-factor. And from what I can
tell, they do a good job keeping up with updates. For 99.9% of people out
there, this doesn't matter. I'm one of those types that like the flexibility to
write my own plug-in if the need arises. The second is prior to running a scan,
you can't obtain a list of what is being scanned for beforehand. Again, this
isn't that big a deal, but it is a feature that would be nice if it were
included.
Ratings
Here is how I rate this product:
| Category | Rating | Comments |
|---|---|---|
| Ease of Use | 5 | You can get a fairly comprehensive scan up and running in minutes. |
| Feature Set | 5 | The product's features work as advertised. A very expansive set of scanning options in a simple, easy to understand interface. |
| Lack of Bugs | 5 | Minor issue with the name, but NGS fixed this bug within 24 hours. |
| Value | 5 | If you need a security scanner, this is a great product. |
| Technical Support | 5 | The only bug I found was corrected within 24 hours of the vendor being notified of it. |
| Documentation | 4 | The product documentation was light, but covered everything needed to use Typhon III. Documentation on vulnerabilities and issues was good. |
| Performance | 5 | Overall this product performs well. It is a very fast scanner, which is critical if you've got a large number of systems to examine. |
| Installation | 5 | A smooth install. Very quick turn around time to get the license key and I was up and running. |
| Learning Curve | 5 | This product is very intuitive and except for the fact I needed to rate the documentation, I didn't refer to the docs when running the tool. |
Product Information
Typhon III is available from Next Generation Software.
| Product: | Typhon III |
|---|---|
| Company: | Next Generation Software |
| Version: | 3.0 |
| Single License Price: | Contact sales@ngssoftware.com |
| Vendor's Product Page: | http://www.nextgenss.com/typhon.htm |
© 2004 by K. Brian Kelley. http://www.truthsolutions.com/ Author of Start to Finish Guide to SQL Server Performance Monitoring (http://www.netimpress.com). |

